Don't Fall for These Three COVID-19 Scams
Category
Awareness, Social Engineering
Risk Level
As the world continues to manage its response to the novel coronavirus (COVID-19), hackers have also continued to exploit the global pandemic. And while their work had previously focused on only the pandemic itself, they have moved on to new subjects that have come from our new normal. Here are three things you need to watch out for this week:
Hackers are pretending to CARE
On March 27, the United States Government signed into law the CARES Act. Part of the law stipulates that many Americans will receive a supplemental stimulus check from the federal government in response to the pandemic. As we’ve talked about before, hackers love taking advantage of government money. In this case, researchers at Cisco Talos have found that hackers are setting up fake websites with “information” about the stimulus checks, or claiming to be able to get the money to you sooner.
It should go without saying that these sites are fake, and will either steal your personal information, install malware on your device, or both. As a side note, eligible Americans will receive a check in the mail, and if you’re wondering about the amount, the Washington Post has pulled together a good calculator that breaks down the legislation.
Hackers are handing out loans
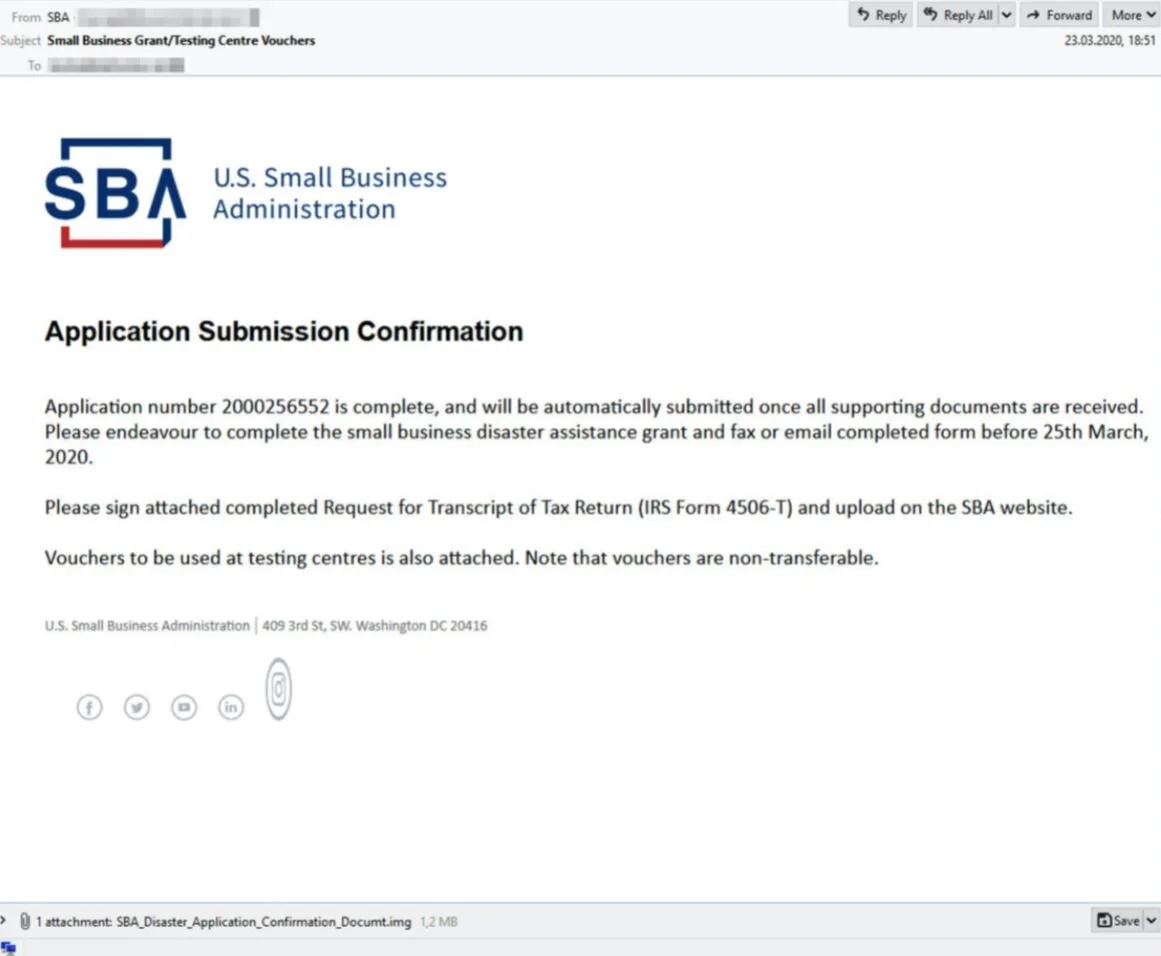
But not really. As many small businesses are struggling to keep their finances in order, researchers at IBM X-Force found that hackers are posing as officials at the U.S. Small Business Administration. This includes sending phishing emails about small business loans related to the pandemic, like the one below:
Courtesy IBM X-Force Threat Intelligence
More concerning, the researchers have noted in the past 14 days a 14,000 percent increase in spam related to the COVID-19 pandemic. So stay alert, and when in doubt, don’t click on any email links and instead, visit the website directly in your internet browser.
Hackers are zooming to install malware
With most of the world’s workforce now working remote, teleconferencing company Zoom has seen a dramatic rise in popularity. From facilitating meetings to offering remote workouts, Zoom has been the go-to service. Naturally hackers have sought to exploit this, with researchers at Check Point noting a skyrocketing number of fake domains meant to impersonate Zoom. As a result, you may end up visiting a link thinking you’re installing the Zoom app on your computer, but instead you are installing malware.
If you are attending a Zoom meeting, this is a good chance to remind you to always make sure to check the URL. In this case, you should be going to https://zoom.us/join and nowhere else.
“What else can I do?”
Be cautious with emails and files received from unknown senders, especially if they are offering special deals or discounts. 90% of cyberattacks start with a phishing email.
Don’t open unknown attachments or click on links within the emails.
Beware of lookalike domains, spelling errors in emails and websites, and unfamiliar email senders.
Ensure you are ordering goods from an authentic source. One way to do this is NOT to click on promotional links in emails, and instead, Google your desired retailer and click the link from the Google results page.
Have a question about an email, phishing, or just cybersecurity in general? Email us at cyberhelp [at] hivesystems.io and we’ll do our best to help you solve your issue!




It's the 2024 update to our Hive Systems Password Table - including using a new “most-hacked” password hash. See why our Password Table has been shown and written about on the news, published by universities, and shared by companies across the globe. Learn more and download your copy!