Let’s Go Phishing
Category
Cybersecurity Fundamentals, Guides
Risk Level
The professional service industry’s rapid and sustained transition to a remote, decentralized workforce has been nothing short of impressive. Teams are supporting each other around the clock and around the globe to deliver on client projects. The critical flaw? People aren’t taking the time to verify the authenticity of email senders and often click on links, open attachments, or even fill out forms without a second of thought. Every errant click runs the risk of completely grinding your company to a halt. How? Through phishing.
“Back up. What’s phishing again?”
Phishing is a specific type of cyber attack through which hackers and scammers use email to trick you. It’s part of a broader cyber attack called “social engineering” that includes other avenues like phone calls, text messages, and even impersonating people in real life. Why? In an attempt to gain personal data. Oftentimes, you’re not even being targeted individually, but rather swept up in a wider attempt to gather information. You probably are already familiar with these concepts, but you may also know all of these by their more common name: a scam.
“Who’s at risk?”
Unfortunately, anyone and everyone at a targeted company who has an email address. Even more startling is that senior and executive managements end up being the most susceptible due to their volume of emails, combined with their limited time to verify senders and/or the email’s contents.
“How does an attack happen?”
There are a number of ways that a person or a company can become the victim of a phishing attack. That said, a typical breach will occur in the following way:
A hacker or scammer gains access to a company’s internal email address list, or is able to ascertain how addresses are formatted (e.g., F.Lastname, or Lastname.Firstname, etc.).
The hacker or scammer will then create an email mimicking either a mundane internal company email blast (e.g., “You forget to submit your timesheet, click here”) or an external marketing solicitation (e.g., “Track your Amazon package”).
This email is then simultaneously sent out en masse to all known company email addresses in the hopes that a just few unsuspecting targets click the malicious link and enter critical information before the attack is flagged and shut down.
The criminal then uses the acquired information to either further penetrate a company’s security protocols (e.g., using stolen usernames and passwords), or profits from the sale of information. Even worse, they may install malware and bring your company to a standstill.
“Are all attacks the same?”
No, and that’s the tricky part. Phishing messages are meant to look like they're coming from a known or trusted source (e.g., a vendor, or a manager). That said, there are typically two intentions for an attack: 1) seeking to steal financial or personal information; or 2) hoping to gain system access credentials. Either of these efforts can be carried out through any number of ways, but the following list identifies the methodologies of some phishing attacks:
Spear phishing
Here things get personal. With this type of phishing attack, emails are personalized with information unique to the victim to entice them. It can include passably familiar information, such as the name of a boss or colleague, or might even reference the name of your bank, or even an old password you’ve used.
Whale attacks
Take a page from Vegas’ book. This type of attack seeks to concentrate its efforts at the highest level of an organization. The hope is that an executive-level officer, or their administrative assistant, are too busy to investigate the details of an email, and will click and enter information for the sake of expediency, never stopping to ensure its validity. Once access has been granted, it’s a digital treasure trove of potentially compromising personal and sensitive corporate information that could destroy the company’s hard earned reputation.
Pharming
This unique type of attack is less common, but it’s just as harmful. Here, a user is redirected from a legitimate site to a malicious replicate site and prompted to enter login credentials or other compromising personal information. Like harvesting crops, the credentials are “harvested” and then used to maliciously access the real site.
Cloud phishing
This method piggybacks on spear phishing but uses actual and authentic messaging specific to cloud based services (e.g., Google drive, Dropbox, OneDrive, or DocuSign) to lure the victim into trusting a malicious link.
“What’s the big deal?”
Well, aside from the certainty of reputational harm associated with the breach of a company’s cybersecurity, it comes down to cost. On average, some $17,000 USD was lost every minute in 2020 as a result of phishing attacks. These costs can range from a few hundred dollars per customer in legal damages awarded to those customers whose data was leaked, to tens of thousands of dollars in ransomware payments to unlock data. Don’t forget that all the while your company is addressing a phishing incident, you’re likely not bringing in revenue. You can read more about the costs of ransomware in another ACT post. Malicious links, attachments, and forms expose personal information and stop your company’s business in its tracks.
“How can phishing breaches be prevented?”
This can be fairly easy, but relentless work. The easy part centers around slowing down and taking the time to verify both the authenticity of the sender, and the validity of links, attachments, or forms that you’re sent; learning to spot red flags, like a sudden urgency to “update your password now.” The difficult part, however, is that you and your company have to constantly be diligent. A link doesn't care if it’s 2:00 PM or 2:00 AM; it’s just waiting for you to let your mind slip for a second and *click*.
Here are just a ways that hackers and scammers can get you to click:
Implied Consensus
“Everyone is volunteering this weekend, so sign up here.”
Authority
“The IRS has requested you update your tax form here.”
Scarcity
“Be one of the first 100 to sign up and get an extra 15% off.”
Familiarity
You recognize the name of the sender and inherently trust that they wanted you to access this Dropbox link. But they must must have forgotten to mention it at the morning meeting.
Intimidation/Urgency
“Click here to make a bitcoin payment in the next 15 minutes or your computer will be erased.”
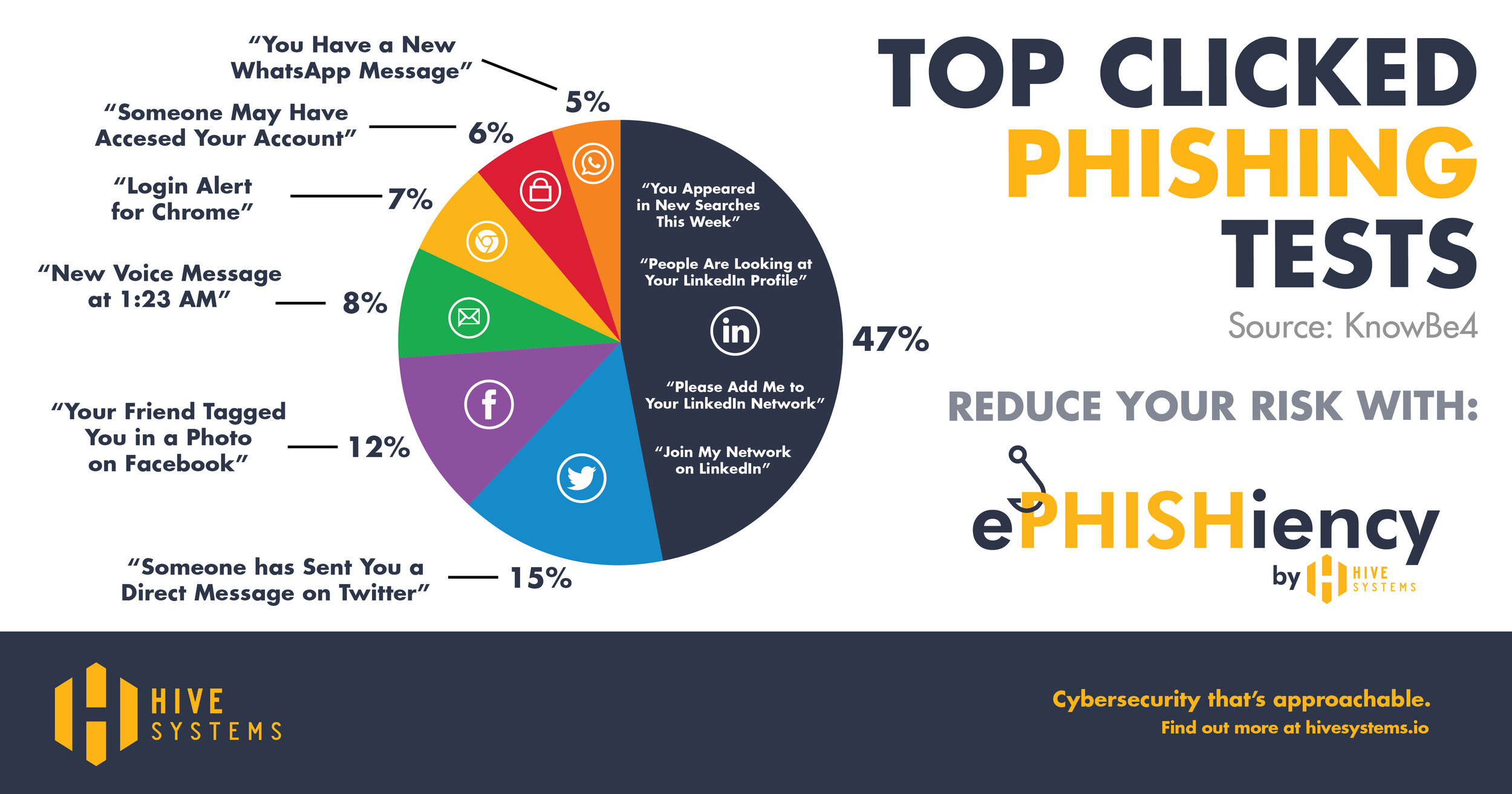
As with any disaster prevention, we recommend the age-old, elementary-school-planned fire drill. That is, take the time to plan and conduct a controlled phishing simulation, using tools like our very own ePHISHiency platform . These drills can help you and your company baseline susceptibility to a phishing attack (i.e. the number of people who click an unknown link), while learning how your employees handle and report suspicious information. Most importantly, it creates educational content in a consequence free environment before disaster actually strikes.
At the end of the day, it comes down to knowing the telltale signs of attacks and constantly taking the time to verify the sender and information before links are clicked.
To spread awareness, you can also download our free Phishing Awareness posters to put up around the water cooler. They come in three different themes, from memorable PSAs to propaganda posters, to a simple, corporate-friendly format.
A note about our platform, ePHISHiency:
Hive Systems believes so fundamentally in the importance of these simulations that we’ve priced our services insanely affordably at $1 per user per month (compared with our industry peers who charge upwards of $8 per user, per month!). Calculate your costs using our estimator. Even better, we take care of everything for you - sending a comprehensive report at the end of every month giving you actionable insights to educate your employees and stay ahead of hackers and scammers.
Still unsure? Contact us today and mention this ACT post for your first three months free.




It's the 2024 update to our Hive Systems Password Table - including using a new “most-hacked” password hash. See why our Password Table has been shown and written about on the news, published by universities, and shared by companies across the globe. How did we make this table? Want to download a copy? Read on!