What is a VPN? And How Does it Work?
Category
Cybersecurity Fundamentals
Risk Level
Maybe you just started working at a new organization and you’re working remote. You can’t access that app someone mentioned, so you ask them and they tell you to “just use the VPN.” What does that mean? And why can you access the app after using the VPN, but you couldn’t before? And what are the impacts or benefits of using it?
“That’s me! But can we back up first?”
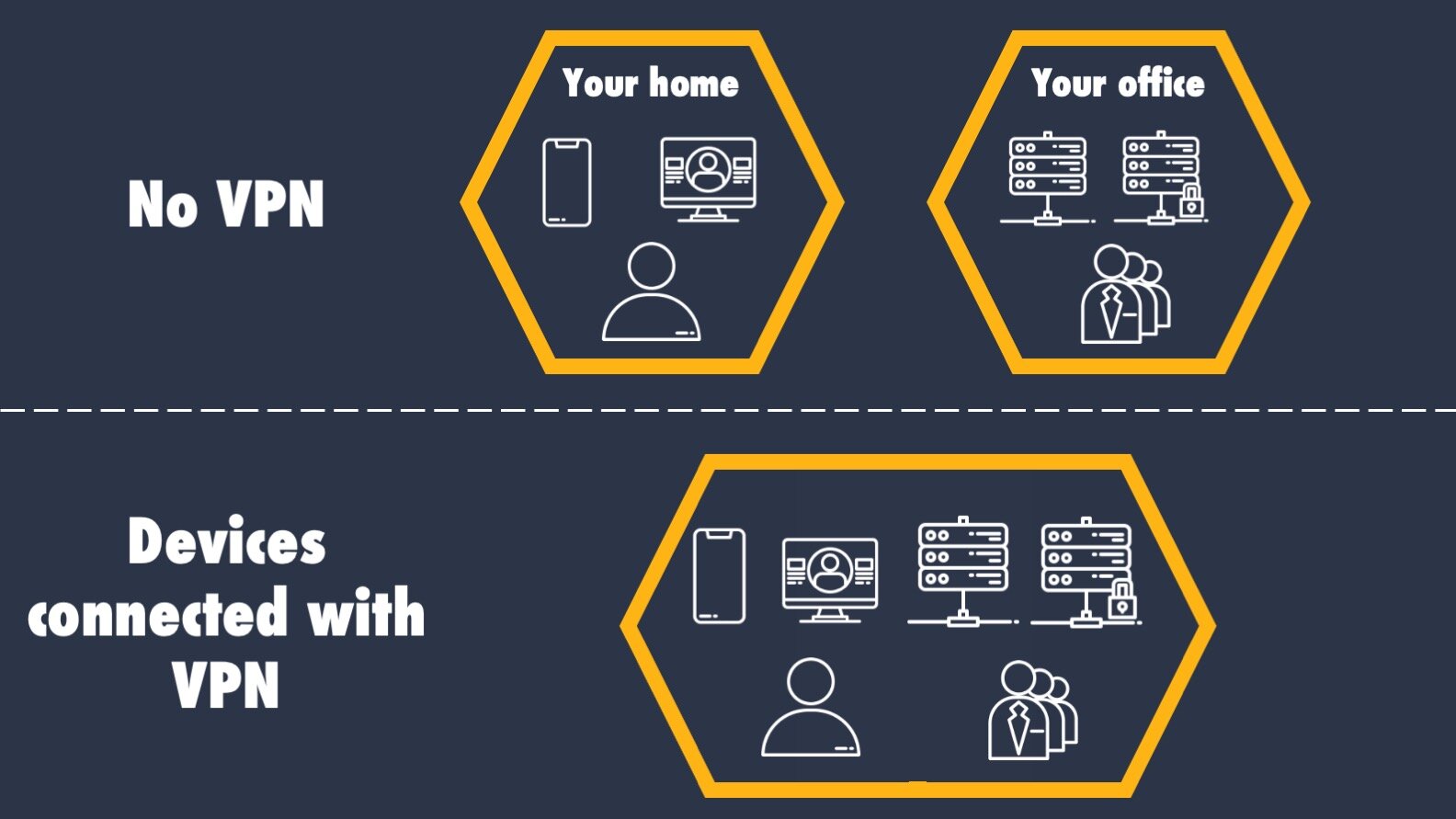
A Virtual Private Network, or VPN, is a technology that allows you to connect your device to another IT network. You may remember from another ACT post that your home Wi-Fi is one IT network, and that at a high level, the internet is made up of many many IT networks that are all connected together.
When you access a website, you are generally talking to the public facing part of an organization’s IT network. For example, when you go to the website of a company, like Hive Systems, you are able to view the content we make available publicly through your web browser. But we have a LOT more servers humming along behind the scenes on our IT network that not only help show you this website, but that also help us conduct business.
Since those servers are inside the Hive Systems network, it means that no one else can access them when they’re not in the office on the network. This is where a VPN comes in. By connecting via a VPN, you are putting your electronic devices, like your computer or phone, in the office - virtually. This gives you access to the same things as if you were sitting at your desk.
For your organization, you may have to logon to your VPN with a password before it connects, but your device may logon automatically. Different organizations choose different approaches, so make sure you understand which option your organization has implemented.
“Are all VPNs the same?”
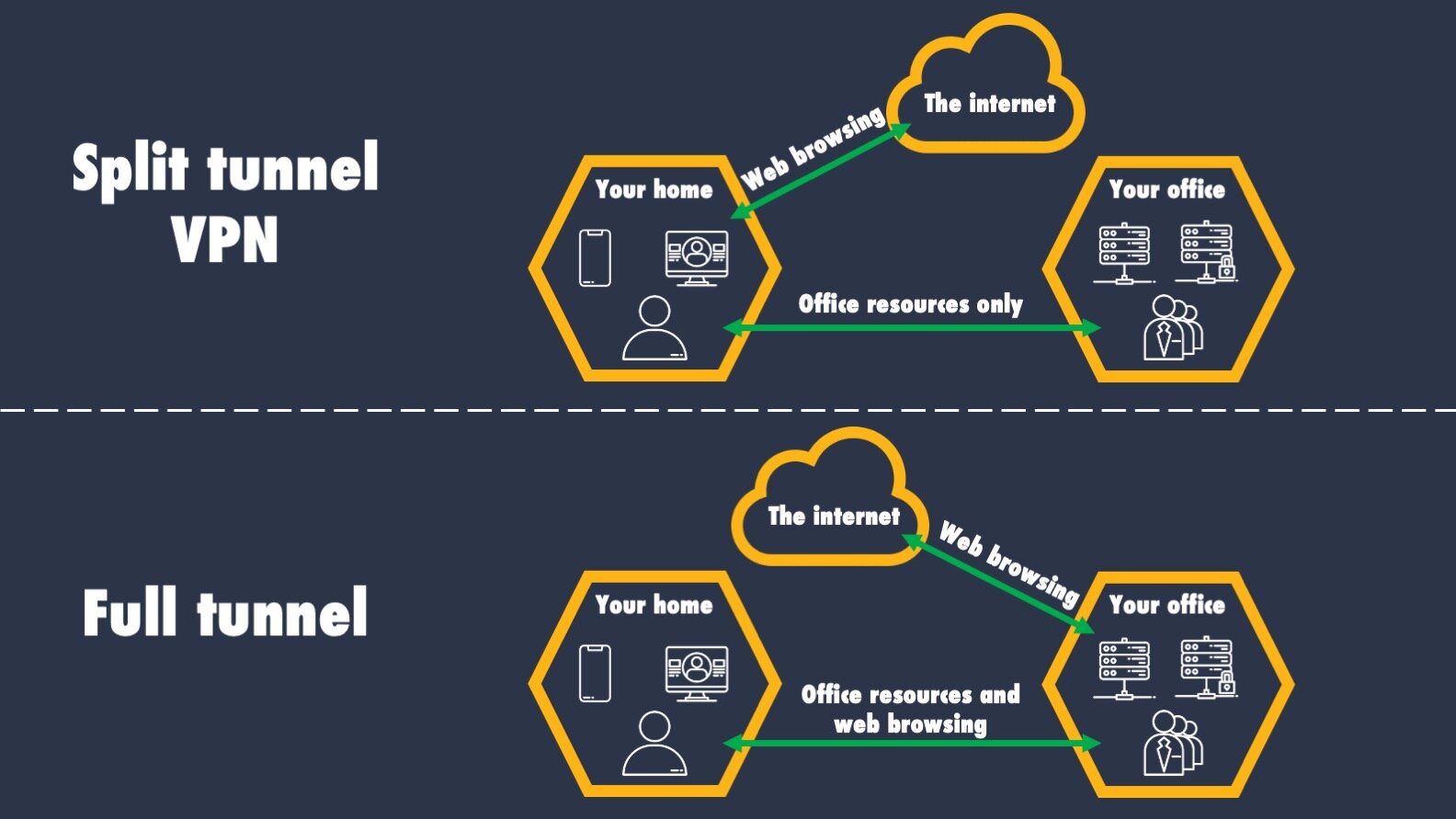
There are two methods that can be used for a VPN: split tunneling and full tunneling.
Split tunneling means that you are able to access your office resources, however when you want to browse the internet, your browsing is not routed through your organization’s IT network. Full tunneling means that all of your internet browsing AND your access to office resources are routed through your organization’s IT network.
What does this mean? It means that if your organization uses full tunneling, that anything you do on your electronic devices is routed through your office. As a result, you may want to be mindful of what you are doing on your electronic devices while connected to your organization’s VPN. Many organizations opt for this model due to the extra security it provides around protecting sensitive information.
Full tunneling requires more data usage, and some organizations prefer to use split tunneling to reduce the internet speed requirements for their office. This is generally the case for smaller organizations. If your organization does use full tunneling, you may experience “slower” internet than your regular internet due to any speed related bottlenecks.
“Ok that makes sense. But my organization leverages the cloud, so how does that change?”
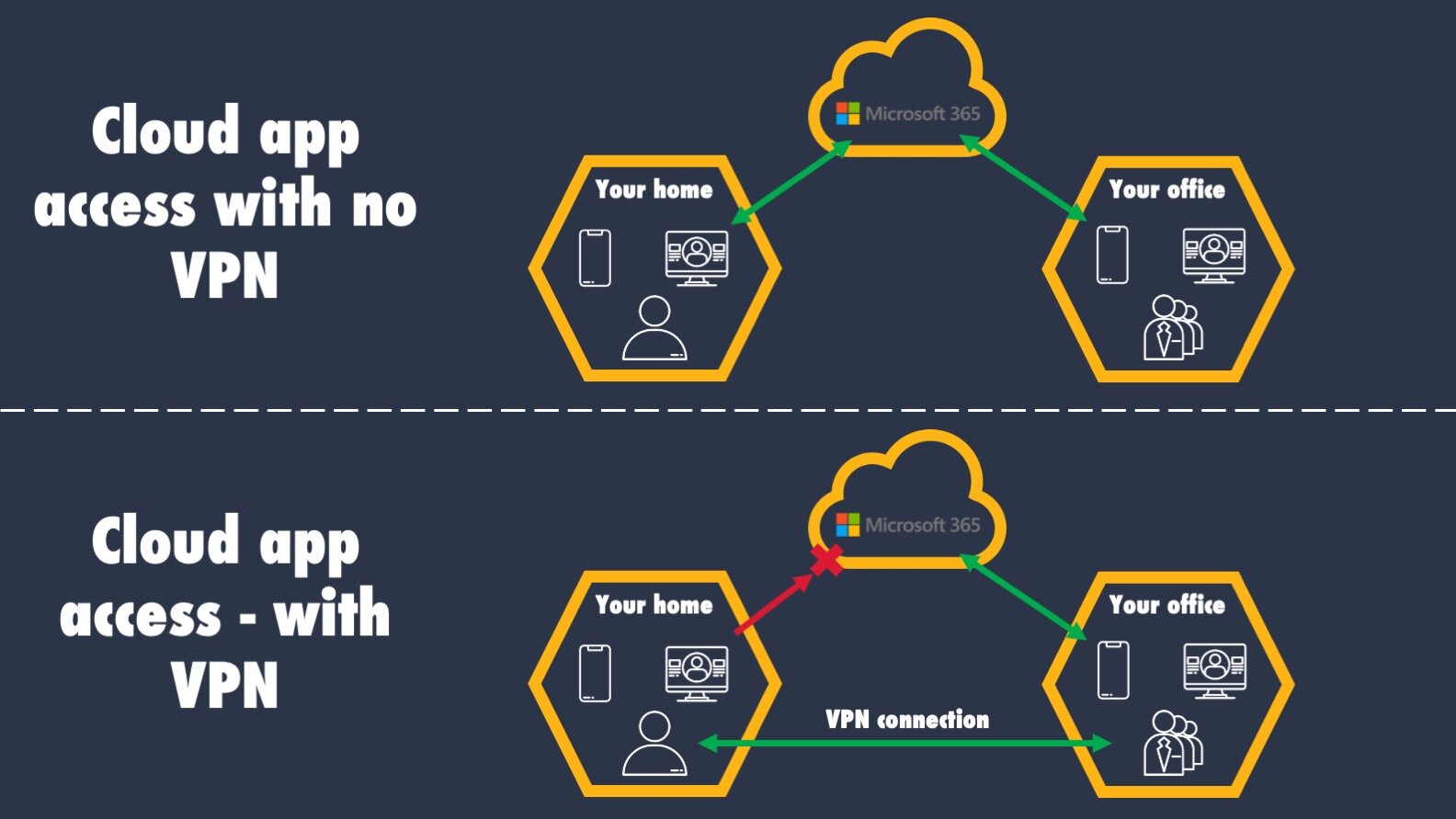
The cloud has presented an interesting change in how organization’s leverage VPNs. In the past, you could most likely only access your organization’s email while on a VPN. But with companies like Google and Microsoft offering cloud based email, you can now access your email anywhere. So are VPNs still necessary? In short: it depends.
Some organization’s have eliminated their office IT networks and have moved completely to the cloud. For smaller organizations, using something like Microsoft 365 may be the best and most cost efficient option. As a result, you would connect directly to Microsoft in the cloud and have access to your organization’s resources; most likely logging onto the website using your email address, password, and hopefully, a multi-factor authentication code.
For larger organizations, they may have specific security requirements, or other processes that require you to access the cloud through the organization’s IT network. In that case, you still connect using a VPN before you’re able to connect to the cloud. As a compromise though, your organization may automatically log you into cloud services like Microsoft 365 through the use of a technology called “single sign-on.”
“Got it, but what about security?”
Ah yes, thanks for asking! VPN’s are great because everything you do on your device while on a VPN is encrypted (check out our ACT post on encryption for a refresh). That means hackers can’t see what you’re doing over the internet while using it - whether connecting to your office, the cloud, or even social media.
In the past, we used to say “never use public Wi-Fi,” which is still a good tip. HOWEVER, if you use a VPN, public Wi-Fi is perfectly safe because the VPN can protect all of your information. As a side note though, this only works for full tunneling, and not split tunneling. So know what kind you’re using?
“So I’m travelling abroad, but I can’t access my favorite Netflix shows. Can I use a VPN to help?”
Just like your organization’s VPN can “put” you in your office virtually, commercially available VPNs can “put” you in another country. This can give you better access to regional websites, services, and yes, even Netflix. While some companies have figured out how to block some VPN providers, you will generally be able to watch your favorite shows.
One caveat: not all commercial VPN providers are equal. Remember how a VPN helps protect everything you do on your device from hackers with encryption? If the VPN provider you choose isn’t reputable, they are likely spying on everything you do. This is absolutely the case for free VPNs - which is why it’s free! Instead, find a company where you can pay for privacy. Usually this means around $5 per month which if you ask us, is absolutely worth it.
And if all of this is confusing, or you’re not sure what VPN option is for your organization, let’s get in touch. An improperly configured VPN may give you false confidence in your security while putting you and your organization at risk. So get in touch today!



It's the 2024 update to our Hive Systems Password Table - including using a new “most-hacked” password hash. See why our Password Table has been shown and written about on the news, published by universities, and shared by companies across the globe. Learn more and download your copy!